When it comes to protecting your cryptocurrency investments it’s important to learn the difference between seed phrase and private key. These two fundamental components have roles in securing your assets making them essential aspects of crypto security. In this blog post we will explore the details of seed phrases and private keys discussing how they are created, why they are important for protecting your funds and ultimately highlighting the variations between them. So grab yourself a cup of coffee. Lets delve into the realm of crypto security!
What is a Seed Phrase?
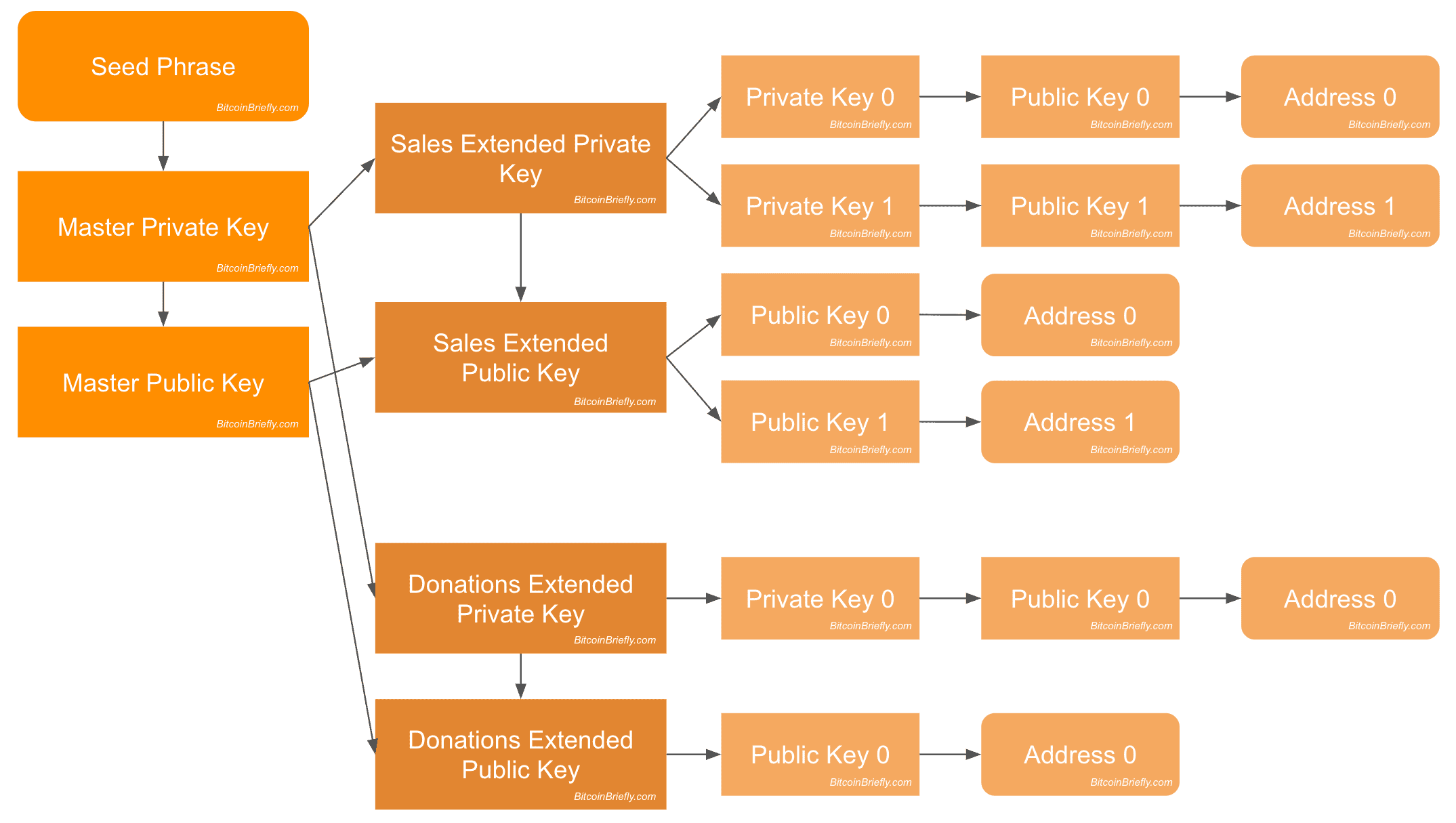
A seed phrase, also referred to as a recovery phrase or mnemonic seed is a string of 12 to 24 words that serves as the key for your cryptocurrency wallet. It acts as a master key that allows you to regain access to your assets in case your wallet is lost, stolen or compromised. This sequence of words represents your key in a manner and can be regenerated when needed.
Creating a seed phrase involves utilizing algorithms to generate a unique set of random words selected from a predefined list. These words are arranged in a sequence to ensure both security and authenticity. Keeping your seed phrase safe and offline is important to having a way to regain control of your funds in situations.
Protecting your seed phrase is essential when dealing with cryptocurrencies. It’s like protecting the key to your domain – make sure it’s kept secure, protected and easily accessible for peace of mind in the changing realm of Bitcoin cash out investments.
How is a Seed Phrase Created?
Creating a seed phrase involves steps to ensure randomness and safety:
- Generating Entropy: A random number (entropy) is produced using methods to ensure unpredictability.
- Converting to Mnemonic Code: The entropy is transformed into a code (consisting of 12 to 24 words) selected from a list of 2048 words ensuring compatibility across wallets.
- Standardization (BIP 39): Adhering to BIP 39 standards for creating codes enables usage across various wallets.
- Word Mapping: Each word in the seed phrase corresponds to a number creating a backup sequence.
- Security and Storage: Keep the seed phrase offline in locations to prevent unauthorized access and facilitate recovery in case of loss or damage.
By comprehending and applying these processes you can protect your cryptocurrency investments. Retain control over assets.
Importance of Keeping Your Seed Phrase Safe
The importance of protecting your seed phrase cannot be overstated when it comes to protecting your cryptocurrency investments.
- Your seed phrase serves as the key to unlocking and managing your assets. Losing it means losing access to your funds
- Treat your seed phrase with care just like you would protect your bank account PIN. It holds the power to control and access all your wealth.
- Keep your seed phrase offline in a location to shield it from theft and unauthorized access amidst the prevalent cyber threats in today’s digital age.
- Protecting your seed phrase guarantees security in the world of cryptocurrencies. Be diligent in its protection, never sharing it online or with strangers.
Make sure to prioritize the security of your seed phrase to mitigate the risk of losing access to your cryptocurrency holdings. Remember, your seed phrase is the key that unlocks independence and security in the realm.
What is a Private Key?
Understanding what a private key is essential for managing cryptocurrency.
A key consists of a unique combination of numbers and letters that functions as a password for accessing and controlling your digital assets on the blockchain similar to a bank account PIN but, with higher stakes.
When you set up a cryptocurrency wallet a unique private key is automatically.
Connected to your public address. This key is essential for signing transactions and proving ownership. Protecting the security and confidentiality of your key is important to keep your assets safe from unauthorized access or theft. If someone gets hold of it they can take control of your funds without any way for you to reclaim them.
To protect your assets it’s important never to share or expose your key online or with anyone you don’t completely trust. By keeping this information confidential you ensure that only you have the power to manage your wealth securely and have peace of mind.
How is a Private Key Generated?
Creating a key for cryptocurrencies involves cryptographic processes to ensure high levels of security.
- Random Number Generation: It all starts with generating a number, which essential for producing an unpredictable private key.
- Hashing Functions: Cryptographic hashing converts the number into a fixed length string ensuring both consistency and security.
- Cryptographic Techniques: Advanced methods such as curve cryptography (ECC) or RSA algorithms manipulate the data to increase complexity and enhance security.
- Output: The end result is an alphanumeric code. The private key. Used as a digital signature, for securely accessing and managing cryptocurrency holdings.
- Randomness and Uniqueness: High levels of randomness are important to ensure that each private key is distinct which is essential for protecting assets against access or theft.
Understanding this process underscores the security measures in place. It is important to protect your key to maintain control over your assets within the decentralized cryptocurrency ecosystem.
Why is the Private Key Important for Crypto Security?
- Control: Serving as a signature the private key grants access to cryptocurrency funds enabling transactions and asset management within the blockchain network.
- Ownership Verification: Utilized in algorithms to generate signatures confirming ownership of transferred assets ensuring secure transactions.
- Protection Against Theft: Protecting the key securely is important; a compromise could result in loss of funds as transactions are immutable and cannot be reversed.
- Analogous to Physical Keys: Just like keys used for safe deposit boxes it’s important to keep keys confidential to prevent unauthorized access and theft.
- Cryptographic Security: Created through algorithms to guarantee uniqueness and security leveraging levels of randomness to thwart guessing or brute force attacks.
- Best Practices for Storage: Storing the offline in hardware wallets or encrypted solutions helps mitigate online threats such as hacking or malware.
Understanding the role of the key and implementing strong security measures is important for protecting digital assets in the decentralized blockchain environment.
Differences Between Seed Phrase and Private Key
Here’s a breakdown of how a seed phrase differs from a key within the realm of cryptocurrency:
Purpose
- Seed Phrase
- Function: Serves as a backup for your cryptocurrency wallet.
- Use: Allows for wallet recovery and retrieval of all associated keys in case of device loss, damage or restoration needs.
- Scope: Acts as the key from which all other keys (including keys) in your wallet are derived.
- Security: Critical for protecting all transactions and assets within your wallet ecosystem.
- Private Key
- Function: Provides access and control to specific addresses in your cryptocurrency wallet.
- Use: Utilized to authorize fund transfers and engage with contracts by signing transactions on the blockchain network.
- Scope: Grants entry to addresses and their corresponding cryptocurrency holdings.
- Security: Important, for managing and overseeing your cryptocurrency assets ensuring that authorized transactions take place.
Format
- Seed Phrase
- Structure: Typically comprises 12 to 24 words arranged in a sequence.
- Storage: Securely storing your data is important whether its, in copy or a secure digital format.
- Private Key
- Format: A series of alphanumeric characters in hexadecimal form must be kept confidential to prevent unauthorized access.
- Usage: It plays a role in signing transactions and proving ownership of cryptocurrency assets securely on blockchain networks.
By understanding these distinctions cryptocurrency users can effectively prioritize security measures to protect their assets in the ecosystem.